Other recent blogs
Let's talk
Reach out, we'd love to hear from you!
SAP Process Integration/Process Orchestration (PI/P0), a critical integration platform developed by SAP, enables businesses to expeditiously unite disparate systems, applications, and data sources. The deep integration capabilities introduced by SAP PI/PO usher in a new era of connectivity and dramatically improve an organization’s capability to innovate and build products at the speed of business.
For modern-day businesses, this integration prowess is not merely a convenience; instead, it is imperative for companies striving to stay agile, adaptive, and resilient in an increasingly complex and interconnected world.
Harnessing the integration capabilities of SAP PI/PO to connect SAP systems with legacy or non-SAP systems and applications leads to data consistency, accelerated decision-making, superior customer experiences, and optimized operational efficiency. And this is not all: in fact, the strategic dismantling of silos within the enterprise also lays the foundation for a more impactful foundation for digital transformation initiatives, enabling companies to create new synergies with the strategic adoption of new and emerging technologies such as Generative AI, Internet of Things (IoT), artificial intelligence (AI), and cloud computing.
SSH keys in SAP PI/PO
SSH keys facilitate seamless and secure access to remote servers and devices over the Internet. In SAP PI/PO, they are used for authentication and encryption purposes, allowing secure transfer of data via protocols like SFTP (SSH File Transfer Protocol) or SCP (Secure Copy Protocol).
SSH keys are seen as a robust alternative to traditional password-based authentication methods, which dramatically improves the overall security and reliability of SAP PI/PO integrations. As the technology relies on cryptographic keys, it becomes increasingly difficult for hackers to tamper with the systems. To fortify their digital security, the SAP PI/PO administrators generate SSH key pairs - usually a public key and a private key.
To securely access or log into the system, you’d need both the keys. While the public key is stored on the SAP PI/PO system, the private key remains with the user or system requiring access. This mechanism not only boosts the overall security but also simplifies the management of user access, making it an integral part of SAP PI/PO's security infrastructure.
Key benefits of SSH keys

Generating and importing SSH keys in SAP PI/PO
Follow these instructions if you’re a novice and willing to learn the entire process of setting up SSH keys in a flash.
Step 1:Generate a brand new SSH key.
- Open Putty Key Gen.
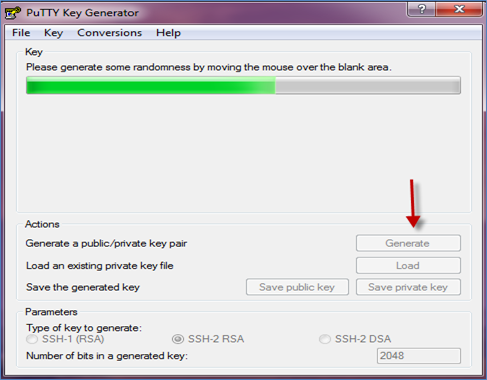
- Click “Generate.”
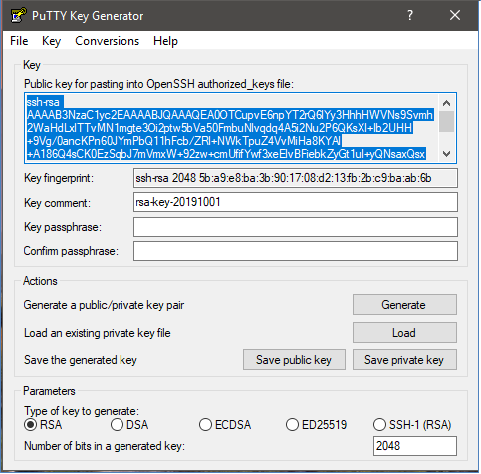
- Below is how the generated key will look like.
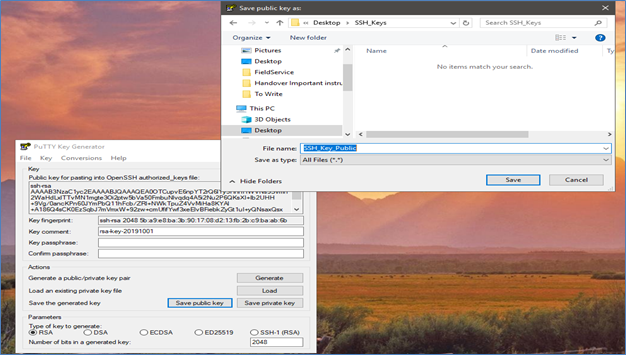
- Save the public and private keys on your system.
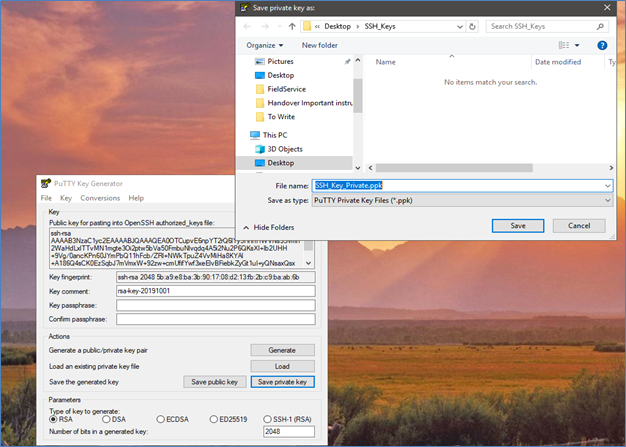
Step 2: Open PuttyGen and load the private key that was exported in Step 1.

- Click “Conversions” and export OpenSSH key.

- Save the file with .pem extension.
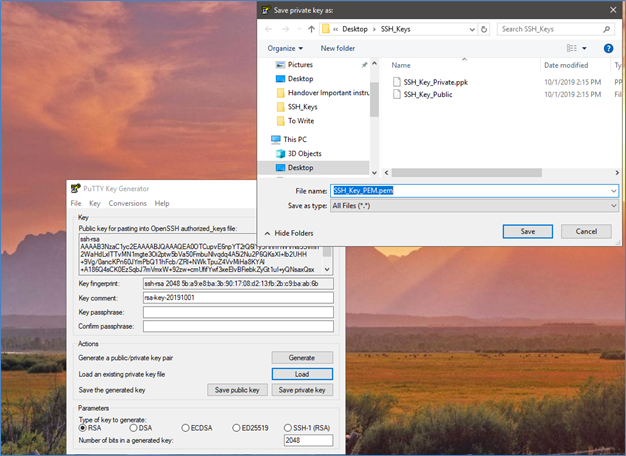
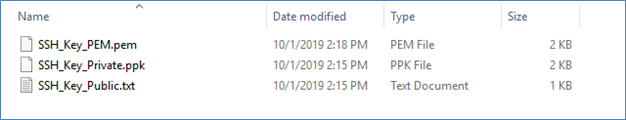
So far, we have generated three keys:
- .pem is the ppk file exported from Putty in “OpenSSHFormat.”
- .ppk is generated from PuttyGen.
- .txt is the public key.
Step 3: If this is the first time you are using Open SSL, you may need to add it to the Environment Variable.
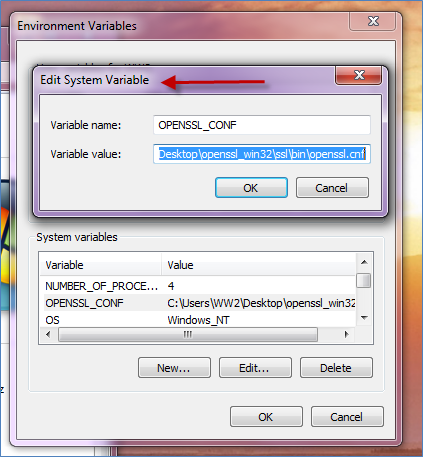
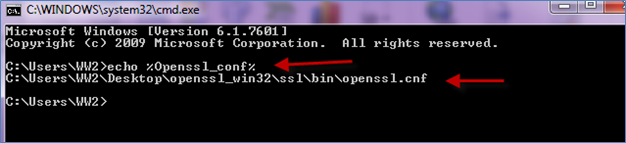
Open command prompt (may need to be in Administrator mode) and test the Variable:
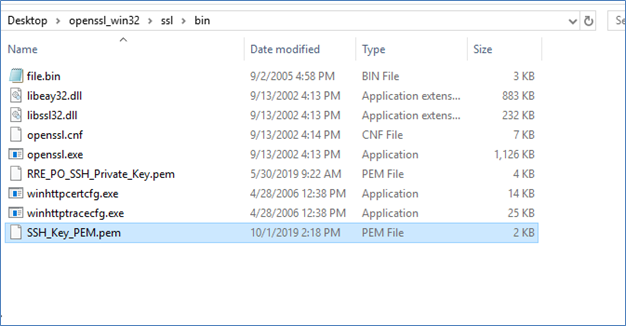
- Copy the .pem version of the private key in Openssl >> Bin Folder.
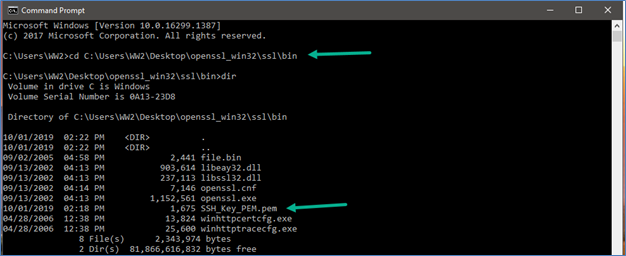
- Open Command Prompt and navigate to Openssl >> Bin Folder.
Specify the command.
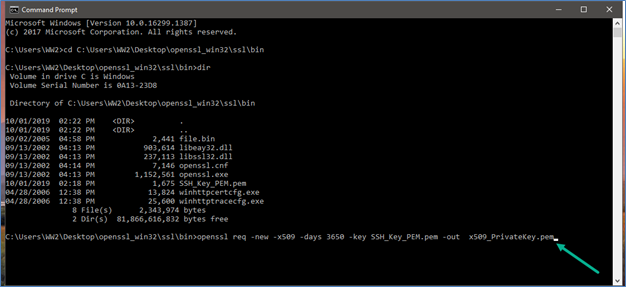
- The command has to be in the below format: openssl req -new -x509 -days 3650 -key <PrivateKey.pem> -out <x509_PrivateKey.pem>
| Note: In the above example, 3650 is used to give 10 years key. If you want to generate two-year key, specify 730 (i.e. 365*2) |
- Going ahead, answer the below questions and soon x509 certificate will be generated.
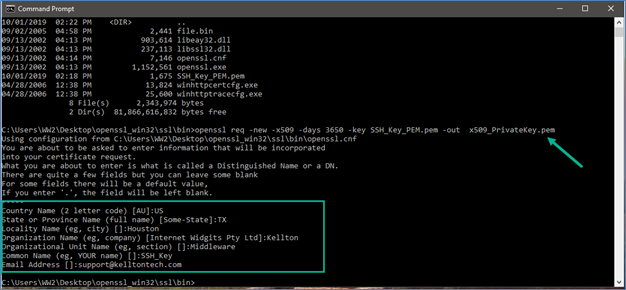
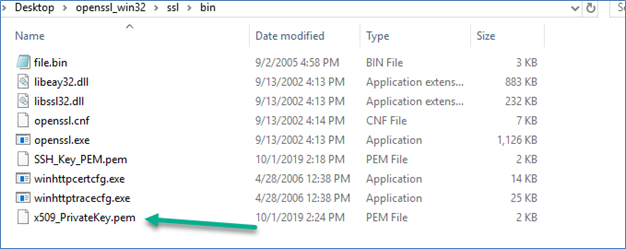
- Now, generate the PKCS12 key for it.
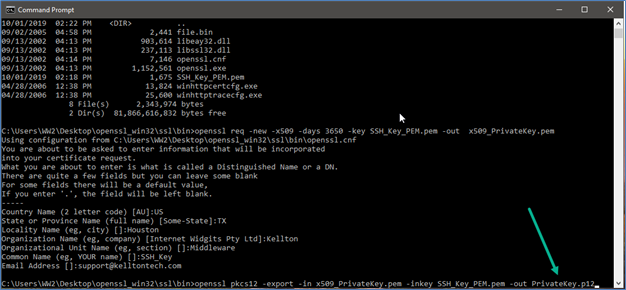
- The command has to be in the below format: openssl pkcs12 -export -in <x509_PrivateKey.pem> -inkey <PrivateKey.pem> -out <PrivateKey.p12>
Step 4: Here, we need to import the PKCS 12 in PI/PO. Login to NWA on PI/PO server and go to “Certificates and Keys: Key Storage.” If you already see a “View” for SFTP, use it or create your own view.

- Click “Import Entry.”
- Select PKCS12 and give the .p12 key name. Specify a password.
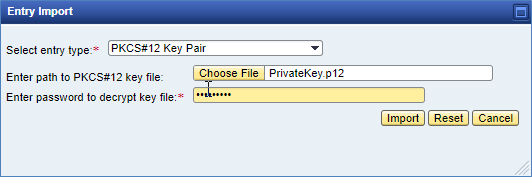
- The key is imported successfully.
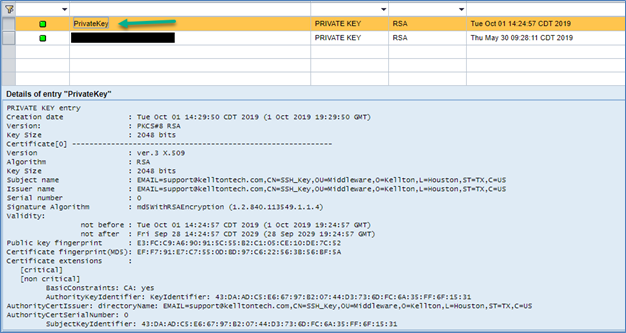
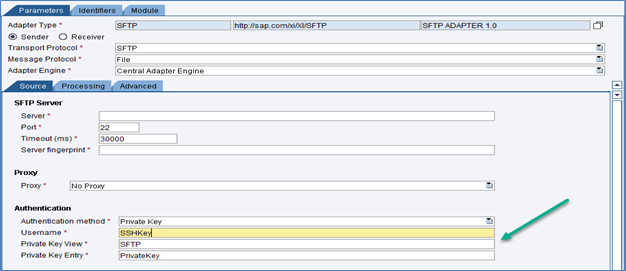
Step 5: Specify this key in the PI/PO Communication Channel as needed.
Wrapping up
SAP PI/PO can be a stepping stone for any organization that plans to evolve into a more integrated and secure enterprise. In the same spirit, SSH keys allow for a secure connection and communication between different systems and applications. Using these keys often leads to a multitude of benefits, such as:
- Improved security: SSH keys provide strong encryption and authentication, reducing the risk of unauthorized access compared to traditional password-based authentication.
- Ease of automation: SSH keys simplify automated processes and scripting by allowing secure access without requiring manual password entry.
- No password management: Users don't need to remember or update passwords, reducing the burden of password management and the risk of weak or compromised passwords.
- Multi-factor authentication: Combining SSH keys with passwords or passphrases creates a robust multi-factor authentication (MFA) system for additional security layers.
- Centralized access control: SSH keys can be centrally managed, making it easier to revoke access, audit user activity, and enforce security policies across a network or infrastructure.
Data breaches are a common occurrence these days. Hackers are using more sophisticated systems and methods than ever before. To keep your organization or sensitive data and systems out of harm’s way, it is pivotal for IT leaders to use SSH keys to secure their integrated systems, applications, and data. We hope the steps shared in this blog help you successfully generate and import SSH keys. If you need any further assistance or have questions, please reach out to our SAP experts.







